在使用 hiveserver2 连接到 hive 时默认是不需要密码的,当然在生产环境可以使用第三方组件如:ranger、kerberos 等来实现对 hive 的权限控制。这里给一个简单的方式来实现使用用户名密码才能连接到 hive
一、原理
本文的原理来自源码中的一个接口
package org.apache.hive.service.auth;
import javax.security.sasl.AuthenticationException;
public interface PasswdAuthenticationProvider {
/**
* The Authenticate method is called by the HiveServer2 authentication layer
* to authenticate users for their requests.
* If a user is to be granted, return nothing/throw nothing.
* When a user is to be disallowed, throw an appropriate {@link AuthenticationException}.
* <p/>
* For an example implementation, see {@link LdapAuthenticationProviderImpl}.
*
* @param user The username received over the connection request
* @param password The password received over the connection request
*
* @throws AuthenticationException When a user is found to be
* invalid by the implementation
*/
void Authenticate(String user, String password) throws AuthenticationException;
}
并且观察该接口的一个实现 CustomAuthenticationProviderImpl
package org.apache.hive.service.auth;
import java.lang.reflect.InvocationTargetException;
import javax.security.sasl.AuthenticationException;
import org.apache.hadoop.hive.conf.HiveConf;
import org.apache.hadoop.util.ReflectionUtils;
/**
* This authentication provider implements the {@code CUSTOM} authentication. It allows a {@link
* PasswdAuthenticationProvider} to be specified at configuration time which may additionally
* implement {@link org.apache.hadoop.conf.Configurable Configurable} to grab Hive's {@link
* org.apache.hadoop.conf.Configuration Configuration}.
*/
public class CustomAuthenticationProviderImpl implements PasswdAuthenticationProvider {
private final PasswdAuthenticationProvider customProvider;
@SuppressWarnings("unchecked")
CustomAuthenticationProviderImpl(HiveConf conf) {
Class<? extends PasswdAuthenticationProvider> customHandlerClass =
(Class<? extends PasswdAuthenticationProvider>) conf.getClass(
HiveConf.ConfVars.HIVE_SERVER2_CUSTOM_AUTHENTICATION_CLASS.varname,
PasswdAuthenticationProvider.class);
PasswdAuthenticationProvider customProvider;
try {
customProvider = customHandlerClass.getConstructor(HiveConf.class).newInstance(conf);
} catch (NoSuchMethodException | InstantiationException | IllegalAccessException | InvocationTargetException e) {
customProvider = ReflectionUtils.newInstance(customHandlerClass, conf);
}
this.customProvider = customProvider;
}
@Override
public void Authenticate(String user, String password) throws AuthenticationException {
customProvider.Authenticate(user, password);
}
}
其逻辑就是如果 hiveserver2 的权限认证是 CUSTOM,会读取配置文件的 hive.server2.custom.authentication.class 配置通过反射的形式实例化并调用 Authenticate;因此赋予 hiveserver2 具有用户名密码的功能只需要在 Authenticate 中实现具体的逻辑就好了。
二、实现
本文采用的是在 hive 的元数据所在的数据库中添加一个 custom_auth 表(因为可以在配置文件中获取到对应的数据库连接信息),将自定义的用户名和密码密文存储其中,在 Authenticate 方法中进行判断即可,
项目依赖如下:
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>org.example</groupId>
<artifactId>hive-auth</artifactId>
<version>1.0-SNAPSHOT</version>
<properties>
<maven.compiler.source>8</maven.compiler.source>
<maven.compiler.target>8</maven.compiler.target>
</properties>
<repositories>
<repository>
<id>io.spring.repo.maven.release</id>
<url>https://repository.apache.org/snapshots/</url>
<releases>
<enabled>true</enabled>
<updatePolicy>always</updatePolicy>
</releases>
<snapshots><enabled>false</enabled></snapshots>
</repository>
</repositories>
<dependencies>
<dependency>
<groupId>org.apache.hive</groupId>
<artifactId>hive-service</artifactId>
<version>3.1.2</version>
<exclusions>
<exclusion>
<groupId>org.glassfish</groupId>
<artifactId>javax.el</artifactId>
</exclusion>
</exclusions>
</dependency>
</dependencies>
</project>
这里的依赖在打包的时候都不需要被打包,编译期间存在即可(hive的lib下都有,包括数据库驱动)
代码如下:
package tech.kpretty.auth;
import org.apache.hadoop.conf.Configuration;
import org.apache.hadoop.hive.conf.HiveConf;
import org.apache.hive.service.auth.PasswdAuthenticationProvider;
import javax.security.sasl.AuthenticationException;
import java.nio.charset.StandardCharsets;
import java.security.MessageDigest;
import java.sql.*;
/**
* @author wjun
* @date 2022/7/18 17:12
* @email wjunjobs@outlook.com
* @describe 自定义 hiveserver2 权限
*/
public class CustomPasswdAuthenticator implements PasswdAuthenticationProvider {
private static final String METADATA_URL_CONF = "javax.jdo.option.ConnectionURL";
private static String METADATA_URL;
private static final String METADATA_DRIVER_CONF = "javax.jdo.option.ConnectionDriverName";
private static String METADATA_DRIVER;
private static final String METADATA_USERNAME_CONF = "javax.jdo.option.ConnectionUserName";
private static String METADATA_USERNAME;
private static final String METADATA_PWD_CONF = "javax.jdo.option.ConnectionPassword";
private static String METADATA_PWD;
private static final String AUTH_SQL = "select 1 from custom_auth t where t.user_name = ? and t.pwd = ?";
public CustomPasswdAuthenticator() {
Configuration configuration = new Configuration(new HiveConf());
METADATA_URL = configuration.get(METADATA_URL_CONF);
METADATA_DRIVER = configuration.get(METADATA_DRIVER_CONF);
METADATA_USERNAME = configuration.get(METADATA_USERNAME_CONF);
METADATA_PWD = configuration.get(METADATA_PWD_CONF);
}
@Override
public void Authenticate(String user, String password) throws AuthenticationException {
try (Connection connection = initConnection()) {
PreparedStatement ps = connection.prepareStatement(AUTH_SQL);
ps.setString(1, user);
ps.setString(2, md5(password));
ResultSet rs = ps.executeQuery();
if (!rs.next()) {
throw new AuthenticationException("用户名或密码不正确!!!");
}
} catch (SQLException throwables) {
throw new RuntimeException("数据库连接异常");
}
}
private static Connection initConnection() {
try {
Class.forName(METADATA_DRIVER);
return DriverManager.getConnection(METADATA_URL, METADATA_USERNAME, METADATA_PWD);
} catch (Exception e) {
throw new RuntimeException(e);
}
}
// md5 32位小写加密
private static String md5(String inStr) {
MessageDigest md5;
try {
md5 = MessageDigest.getInstance("MD5");
} catch (Exception e) {
e.printStackTrace();
return "";
}
byte[] byteArray = inStr.getBytes(StandardCharsets.UTF_8);
byte[] md5Bytes = md5.digest(byteArray);
StringBuilder hexValue = new StringBuilder();
for (byte md5Byte : md5Bytes) {
int val = ((int) md5Byte) & 0xff;
if (val < 16) {
hexValue.append("0");
}
hexValue.append(Integer.toHexString(val));
}
return hexValue.toString();
}
}
三、实施
将上述代码打包放入 hive 的 lib 下,修改 hive-site.xml 配置文件,添加如下配置
<property>
<name>hive.server2.authentication</name>
<value>CUSTOM</value>
</property>
<property>
<name>hive.server2.custom.authentication.class</name>
<value>tech.kpretty.auth.CustomPasswdAuthenticator</value>
</property>
在 hive 元数据的数据库中建表
create table custom_auth
(
user_name varchar(10),
pwd varchar(32)
);
插入自定义用户名和密码密文,密文这里采用 md5 32位小写加密;最简单的方式就是跑一下代码里面的 md5 方法
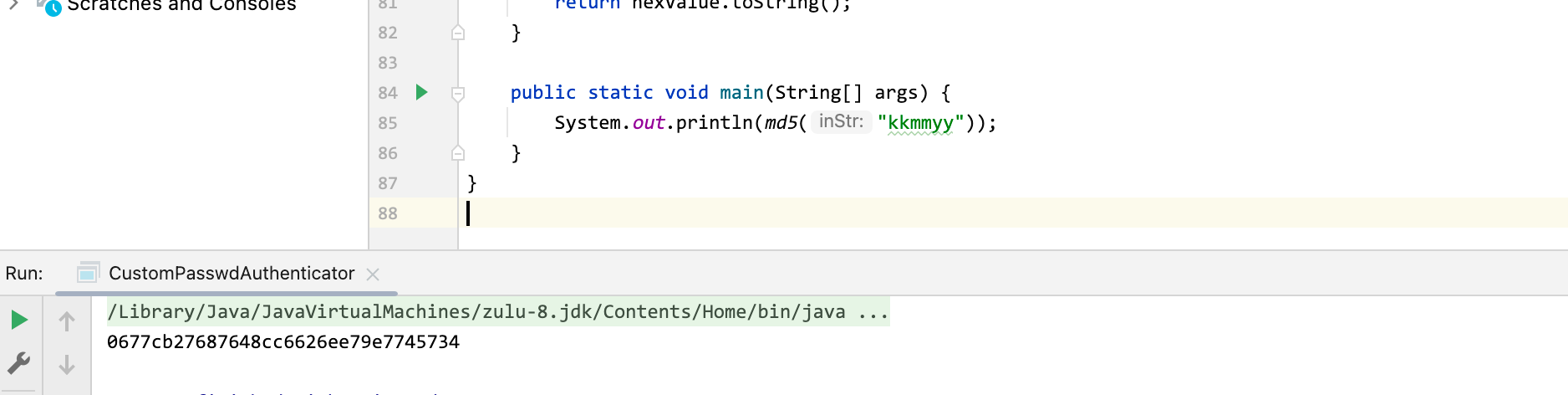
重启 hiveserver2 即可
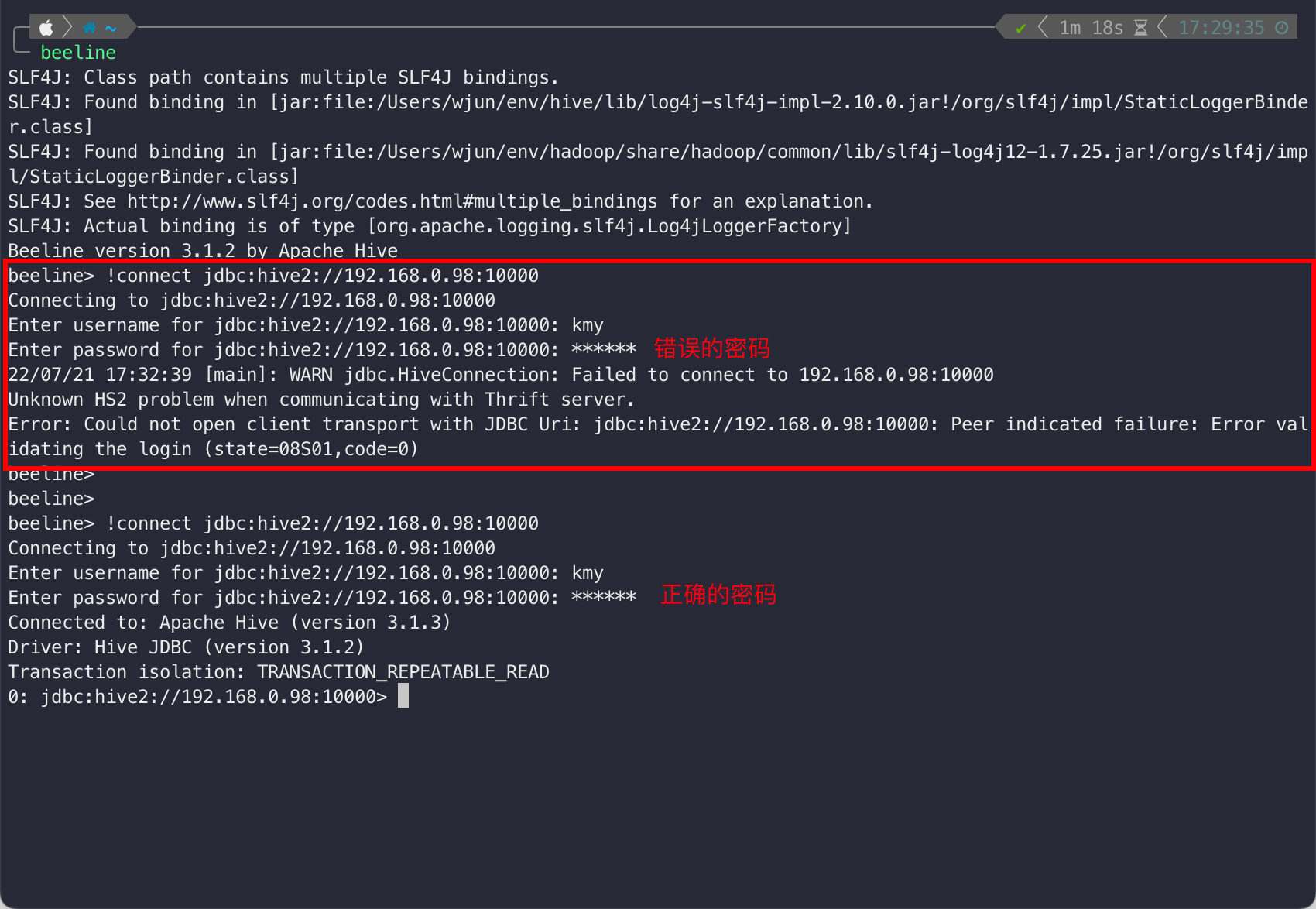
测试结果如下


评论区